長期運用していたアプリケーションのセキュリティチェックをしようと sensiolabs/security-checker を使おうとしたのですがアーカイブされて使えませんでした。代替えとして2種類のライブラリがあったのですが、Symfony CLI を使ってみたのでメモしておきます。
Symfony CLI のダウンロード方法はこちらから
LinuxやMacの方はcurlで使えるようになります
$ curl -sS https://get.symfony.com/cli/installer | bash
Symfony CLI installer
Environment check
[*] cURL is installed
[*] Tar is installed
[*] Git is installed
[*] Your architecture (amd64) is supported
Download
Downloading https://github.com/symfony-cli/symfony-cli/releases/latest/download/symfony-cli_linux_amd64.tar.gz...
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0
100 5176k 100 5176k 0 0 3048k 0 0:00:01 0:00:01 --:--:-- 100M
Uncompress binary...
Installing the binary into your home directory...
The binary was saved to: /home/<user>/.symfony5/bin/symfony
The Symfony CLI was installed successfully!
Use it as a local file:
/home/<user>/.symfony5/bin/symfony
Or add the following line to your shell configuration file:
export PATH="$HOME/.symfony5/bin:$PATH"
Or install it globally on your system:
mv /home/<user>/.symfony5/bin/symfony /usr/local/bin/symfony
Then start a new shell and run 'symfony'PATHを通すなりバイナリを移動するなりしてコマンドを使えるようにしましょう。
あとは composer.lock が置かれているディレクトリで symfony security:check を実行すればセキュリティ的にマズいパッケージを使っていないか確認できます。
こちらは最新で問題ない場合の表示
$ symfony security:check
Symfony Security Check Report
=============================
No packages have known vulnerabilities.
Note that this checker can only detect vulnerabilities that are referenced in the security advisories database.
Execute this command regularly to check the newly discovered vulnerabilities.そしてこちらは2年前に作ったLaravelアプリケーション
% symfony check:security
Symfony Security Check Report
=============================
4 packages have known vulnerabilities.
guzzlehttp/guzzle (7.4.1)
-------------------------
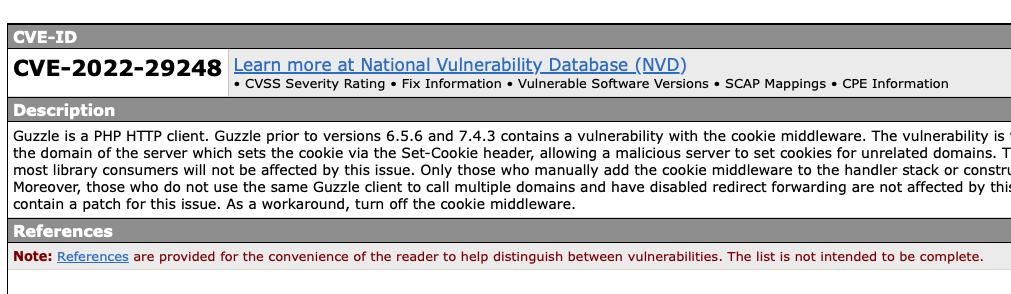
* [CVE-2022-29248][]: Cross-domain cookie leakage
* [CVE-2022-31042][]: Failure to strip the Cookie header on change in host or HTTP downgrade
* [CVE-2022-31043][]: Fix failure to strip Authorization header on HTTP downgrade
* [CVE-2022-31090][]: CURLOPT_HTTPAUTH option not cleared on change of origin
* [CVE-2022-31091][]: Change in port should be considered a change in origin
guzzlehttp/psr7 (2.1.0)
-----------------------
* [CVE-2022-24775][]: Inproper parsing of HTTP headers
laravel/fortify (v1.10.0)
-------------------------
* [CVE-2022-25838][]: Multi-Factor Authentication issue in Laravel Fortify
symfony/http-kernel (v5.4.4)
----------------------------
* [CVE-2022-24894][]: Prevent storing cookie headers in HttpCache
[CVE-2022-29248]: https://github.com/guzzle/guzzle/security/advisories/GHSA-cwmx-hcrq-mhc3
[CVE-2022-31042]: https://github.com/guzzle/guzzle/security/advisories/GHSA-f2wf-25xc-69c9
[CVE-2022-31043]: https://github.com/guzzle/guzzle/security/advisories/GHSA-w248-ffj2-4v5q
[CVE-2022-31090]: https://github.com/guzzle/guzzle/security/advisories/GHSA-25mq-v84q-4j7r
[CVE-2022-31091]: https://github.com/guzzle/guzzle/security/advisories/GHSA-q559-8m2m-g699
[CVE-2022-24775]: https://github.com/guzzle/psr7/security/advisories/GHSA-q7rv-6hp3-vh96
[CVE-2022-25838]: https://github.com/advisories/GHSA-6w4v-qr4m-97gg
[CVE-2022-24894]: https://symfony.com/cve-2022-24894
Note that this checker can only detect vulnerabilities that are referenced in the security advisories database.
Execute this command regularly to check the newly discovered vulnerabilities.試しに CVE-2022-29248 でググればどんなセキュリティ的な問題があるのか確認できるので、これを目安にパッケージアップデートしていきます。
お疲れ様でした。
コメントを残す